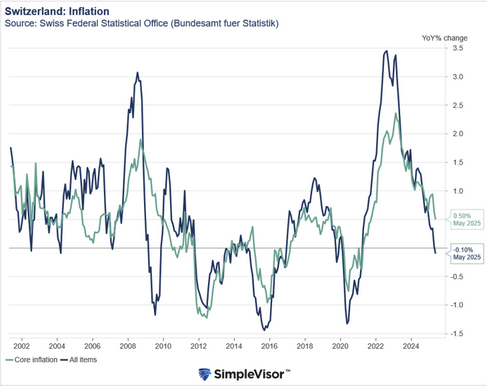
In February, the Swiss government awarded mobile radio frequencies for 5G to three telecom operators: Salt, Sunrise and Swisscom.
As more governments mull the risks of working with foreign vendors of 5G networks, eyes are on Switzerland as one of the technology’s early adopters. Will the Swiss take a heavier hand in restricting foreign providers like Huawei in the 5G supply chain or let the market decide?
In a grim but not-so-far-fetched scenarioexternal link, a hacker attacks a 5G antenna, sending malicious signals to millions of connected devices. It causes a breakdown in the transportation system and energy grid and brings cities to a standstill. This quickly spreads to other countries’ networks, causing a large-scale attack on the global internet.
For all the benefits that the total connectivity enabled by 5G could bring, it also raises the stakes for security as this scenario illustrates. The EU-wide 5G cybersecurity risk assessmentexternal link released last week reiterated this, stating that the dependence of critical services on 5G networks means a major disruption is likely to have particularly serious consequences.
“Any technological change brings opportunities and risks,” says Florian Egloff, a senior researcher at the Center for Security Studies at the federal technology institute ETH Zurich.
Since no Swiss company has the means to supply the infrastructure required for a 5G network Egloff says the country must rely “on foreign technology providers if you’d like to adopt 5G technology”.
The Huawei case
In the case of 5G, the foreign provider that can produce “at scale and costexternal link” all the elements of a 5G network happens to be Chinese telecom giant Huawei.
This has raised fears of cyber espionage by the Chinese government and prompted government measures ranging from outright bans by the US and Australia to proposals for new security protocols in the European Unionexternal link.
The warnings have also echoed in Switzerland. Swiss politicians raised questionsexternal link earlier this year about the risks of working with Huawei.
Switzerland has rolled out hundreds of 5G antennasexternal link in the country, making it one of the world’s 5G pioneersexternal link.
All three major Swiss telecom operators – Salt, Sunrise and Swisscom – are approved to cover the country in 5G, and all have Huawei equipment in their fixed and mobile networks. Sunrise has also contracted Huawei to provide the technology behind the 5G network.
The Swiss government says it is taking security concerns seriously. But it also acknowledges that its hands are somewhat tied.
A spokesperson from the Office of Communications (OFCOM) told swissinfo.ch that “according to the existing legal basis, the government does not have the ability to influence the acquisition of equipment providers by network operators.”
What is 5G?
5G is the next generation of wireless mobile technology, providing greater data speeds, lower latency (better responsiveness), and the possibility to simultaneously connect to more devices. 5G is expected to become what some have called the digital nervous systemexternal link of society.
This is expected to help advance robotics and automation, virtual and augmented reality, and artificial intelligence and machine learning – connecting devices in ways never seen before. For more information about how Switzerland is developing 5G see hereexternal link.
Who is responsible?
So, who is responsible for guaranteeing the technology is safe? While national security is within the government’s purview, legislation doesn’t always keep apace with rapid changes in technology.
For example, Switzerland’s revised telecommunications law approved by parliament in March 2019 includes a specific articleexternal link on cybersecurity, calling on companies to combat any unauthorised manipulation of their telecommunications equipment.
However, neither that legislation nor the latest revision of the law on data protectionexternal link mentions potential threats stemming from contracts with foreign vendors of software or hardware.
“The revised federal telecommunications act was developed at a stage when the topic of foreign providers was not on the agenda,” says Florian Roth, an attorney specialised in telecommunications law at Walder Wyss in Zurich.
There is also a set of non-binding security guidelinesexternal link that date back to 2009.
Switzerland’s revised cybersecurity strategyexternal link also remains rather vague, leaving it up to private actors to put in place measures that it fails to specify, according to Roth.
Roth notes that the approach is typical for the Swiss regulator. “It is very pragmatic. The regulator often delegates to actors on the market to specify which measures are adequate.”
This places much of the responsibility for network integrity in the hands of the telecoms.
There are currently no binding rules for these companies relating to the use of hardware of foreign providers. They also have no legal duty to report a security breach unless it causes major disruptions to service or the network. This may change with the implementation of the revised Swiss data protection act but it isn’t clear when this will come into force.
Both Swisscom and Sunrise told swissinfo.ch that they conduct risk assessments of suppliers and regularly monitor and report threats to the government. Sunrise also indicated that Huawei supplies and operates the systems but the data itself remains with Sunrise.
Swisscom, which is majority state-owned, also said it has exit clauses in all contracts and with all providers. Collaborations also have time limits, typically reviewed and retendered after 5-10 years.
The company also publishes a cybersecurity reportexternal link on a regular basis.
The backdoor problem
However, some cybersecurity experts say these measures may not be enough. One big question relates to so-called “backdoorsexternal link”, or hidden remote access points that can be exploited to gain control of a device.
The EU report states that since 5G networks will be largely based on software, major security flaws could make it easier for actors to maliciously insert intentional backdoors into products and make them harder to detect.
According to an addendumexternal link to the cybersecurity article in the revised telecommunications law, the government stops short of calling on telecom providers to check for physical access and backdoors in hardware and software.
An OFCOM spokesperson told swissinfo.ch that this was left out largely for feasibility reasons as it’s “often not possible for telecom companies since the customer’s computer is located at home or elsewhere.”
Sunrise told swissinfo.ch that “since the first allegations of US politicians against Huawei, no irregularities have ever been detected in Huawei equipment or software, nor has any conclusive evidence been provided to support the allegations against Huawei.” It added that the company does not plan to change Huawei as a supplier.
Cracking down
The reality of dependency on foreign providers for 5G infrastructure has led countries to take precautionary measures. While the US and Australia are on the extreme end by blacklisting Huawei, the EU is mulling other tacticsexternal link to ward off risks, without calling out specific vendors.
The UKexternal link has called on operators to work with vendors on assurance testing and more controls on certain high-risk vendors. Franceexternal link is debating a proposal that would require telecom operators to seek formal permission from the Prime Minister for their 5G network projects.
Some individual operators have also been more cautious in signing contracts with Huawei. The Norwegian telecom provider Telia just announcedexternal link that it has chosen Ericsson over Huawei for its rollout of 5G. The government was quick to say that they didn’t order the company to reject Huawei.
Huawei has repeatedly stated that it would rather shut down than spy for the Chinese government, offering “no-spy agreements” to several governments, most recently Polandexternal link.
Wait and see
For now, the Swiss government appears to be taking a wait-and-see approach, watching what happens first in the EU.
The regulator also must weigh protection of personal privacy and market competition when considering tightening the screws on how the sector manages cybersecurity, says Roth.
There is also the matter of rattling relations with China – one of Switzerland’s most important trading partners.
Overall, Egloff of the ETH Zurich believes that the Swiss government is taking the supply chain concerns seriously.
The latest cybersecurity reportexternal link published in April notes that a general discussion is taking place in the country on how to extricate itself “from dependence on the two de facto technology giants USA and China.” The government also announcedexternal link it is setting up a competency centre on cybersecurity.
But the challenges are immense from both a strategic and technical perspective. A studyexternal link by the Center for Security Studies at the ETH Zurich points out that there remains ongoing ambiguity about the details of relationships with the private sector and a lack of incentives for companies to engage with national security issues.
The question, says Egloff, is “at what point onwards should the state either mandate, invest, or assist companies in the defense of their infrastructure?”
Full story here Are you the author? Previous post See more for Next postTags: Business,newsletter